In AWS IAM, managing user permissions using groups and policies involves creating groups, attaching policies to groups, adding users to groups, and utilizing fine-grained permissions through inline policies. This approach provides centralized control, scalability, and ease of updates for consistent and efficient management of user access to AWS resources.
Scenario:
Kia, launching a startup, an online book store, hired a bunch of developers, and help her to assign access to developers.
Users to developer group access:
\>> Dynamo DB
\>> Lambda
\>> S3 bucker
\>> API gateway
Log in to your AWS console, and click on IAM

When you enter the IAM dashboard, you will all the assigned users.
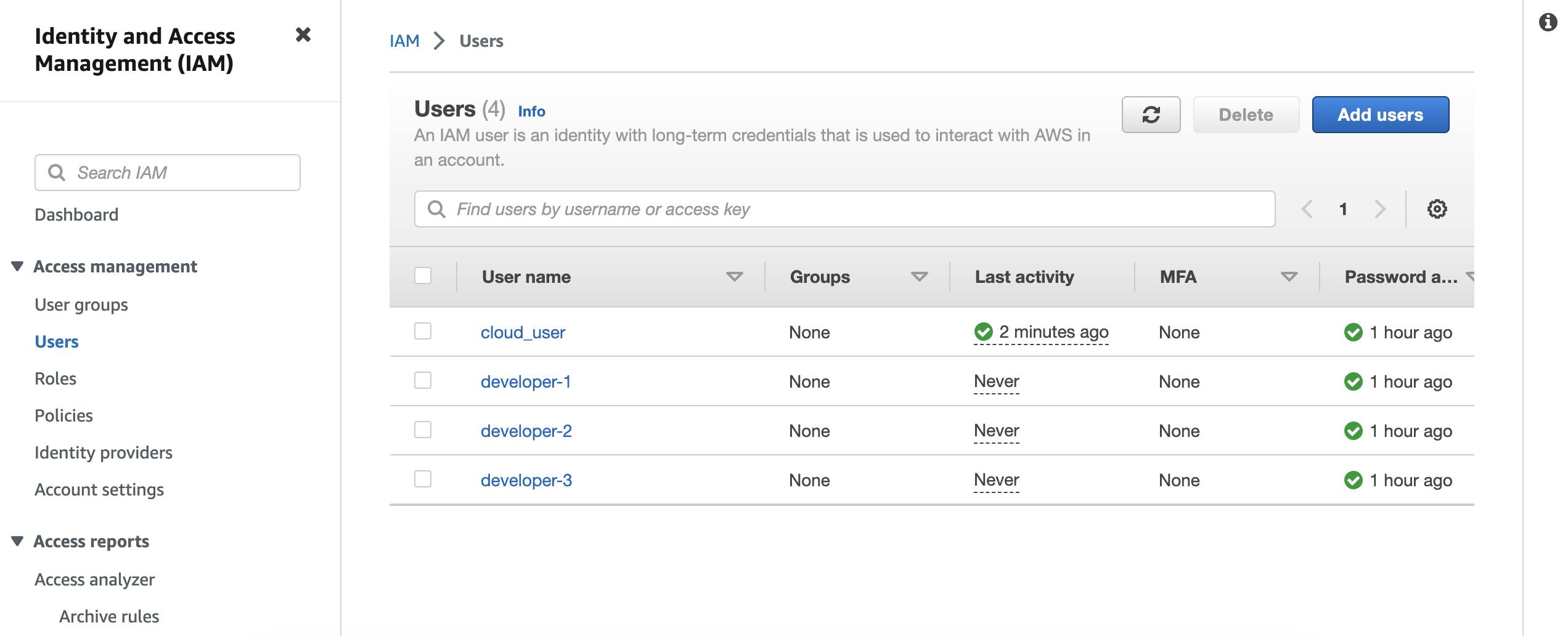
Then click on policies>>
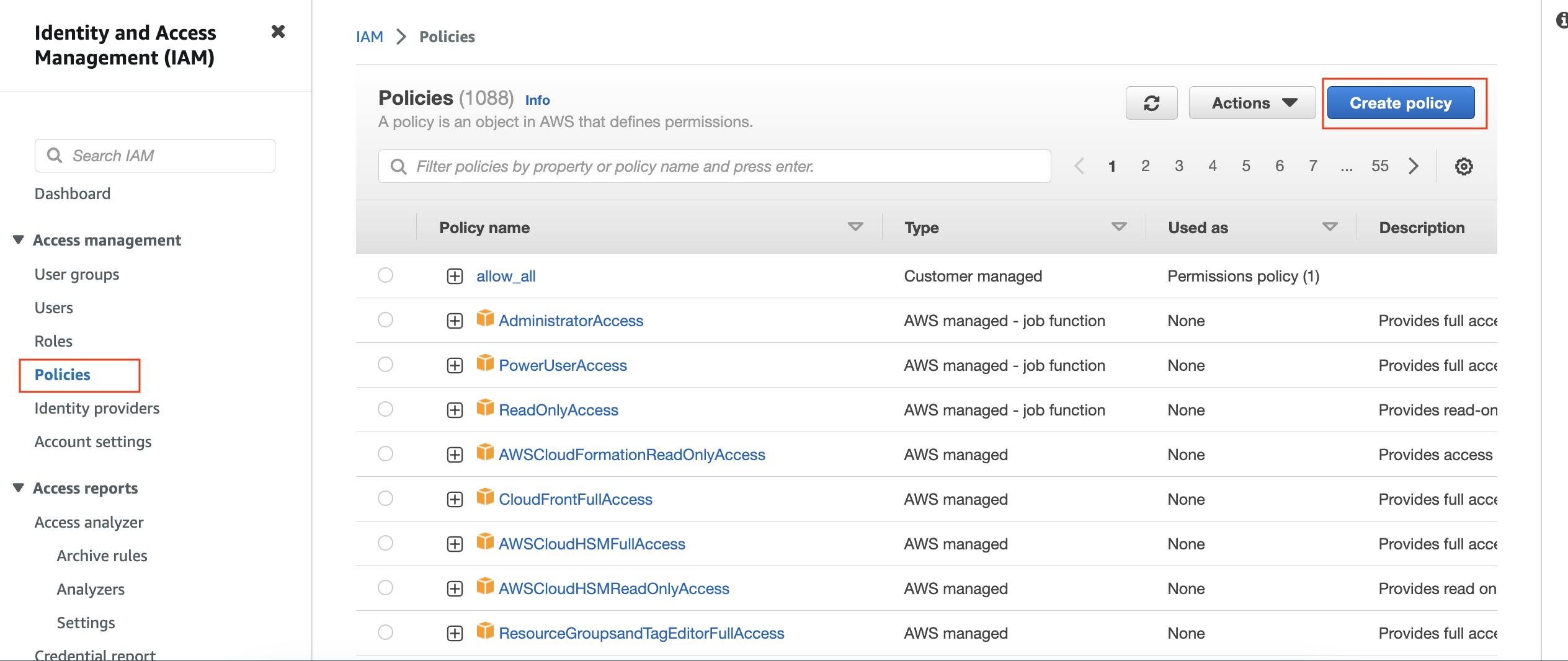
The policies can be written in two formats:
JSON Format: Writing AWS IAM policies in JSON allows for full control and flexibility over the policy document structure, using a structured syntax.
Visual Tools: AWS provides graphical interfaces to visually create and modify IAM policies, making it more accessible for users without JSON knowledge, but with potential limitations and reduced version control.
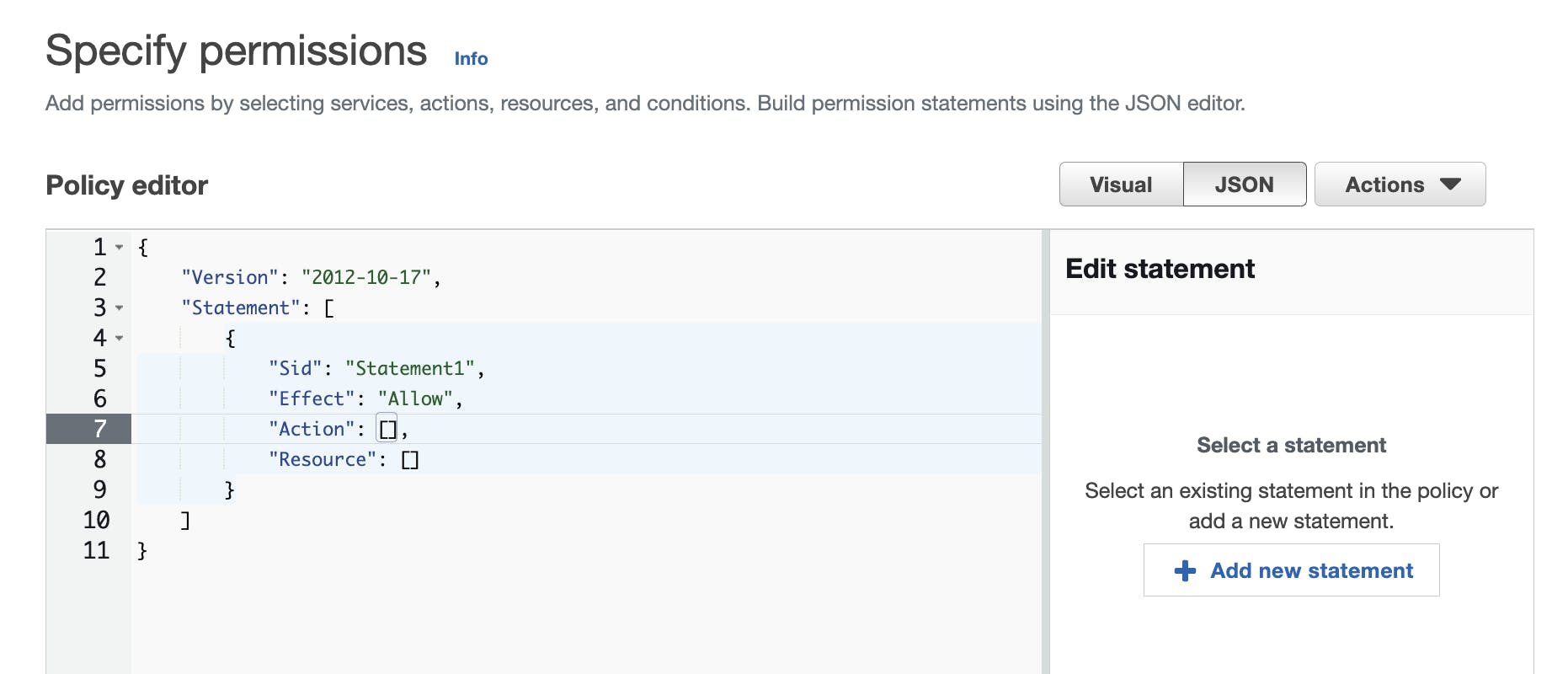

Setting up permission for AWS lambda, AWS DynamoDB, S3 bucker and API gateway for the developers.
#Note: The developer group is not created yet, so we are just creating a policy initially.
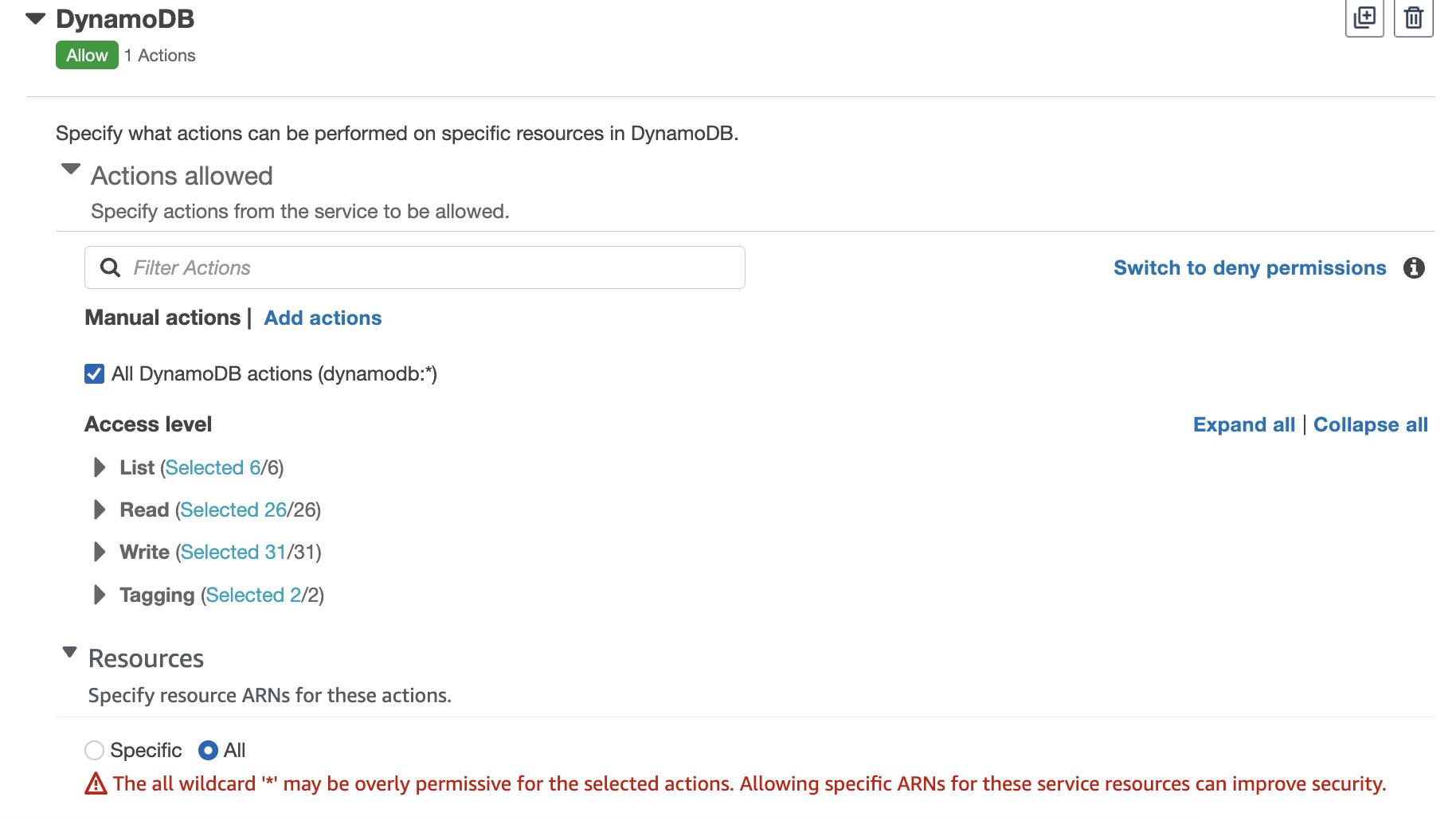
Giving all the permissions.
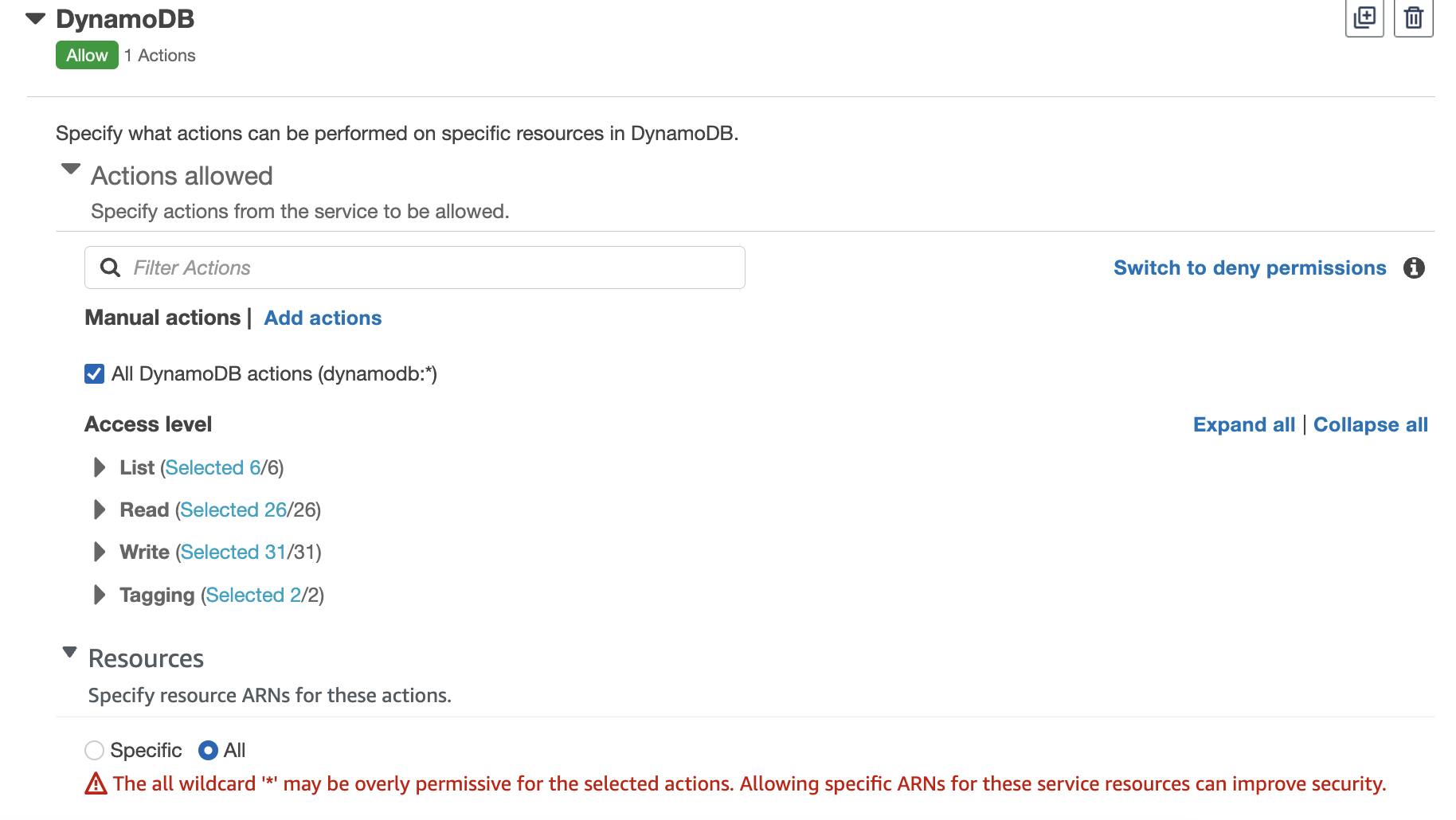
Access to all the resources.
Add all the services one by one.

The next step comes, in naming the policy, which has to be unique and follow standard naming conventions.
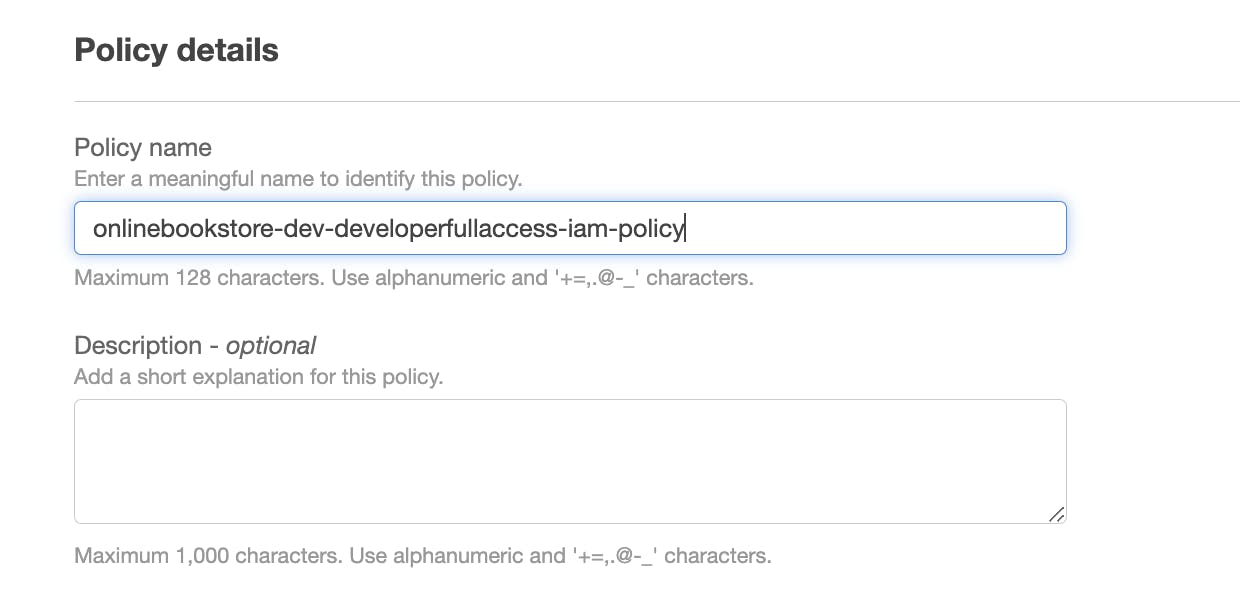
Then click on create policy.
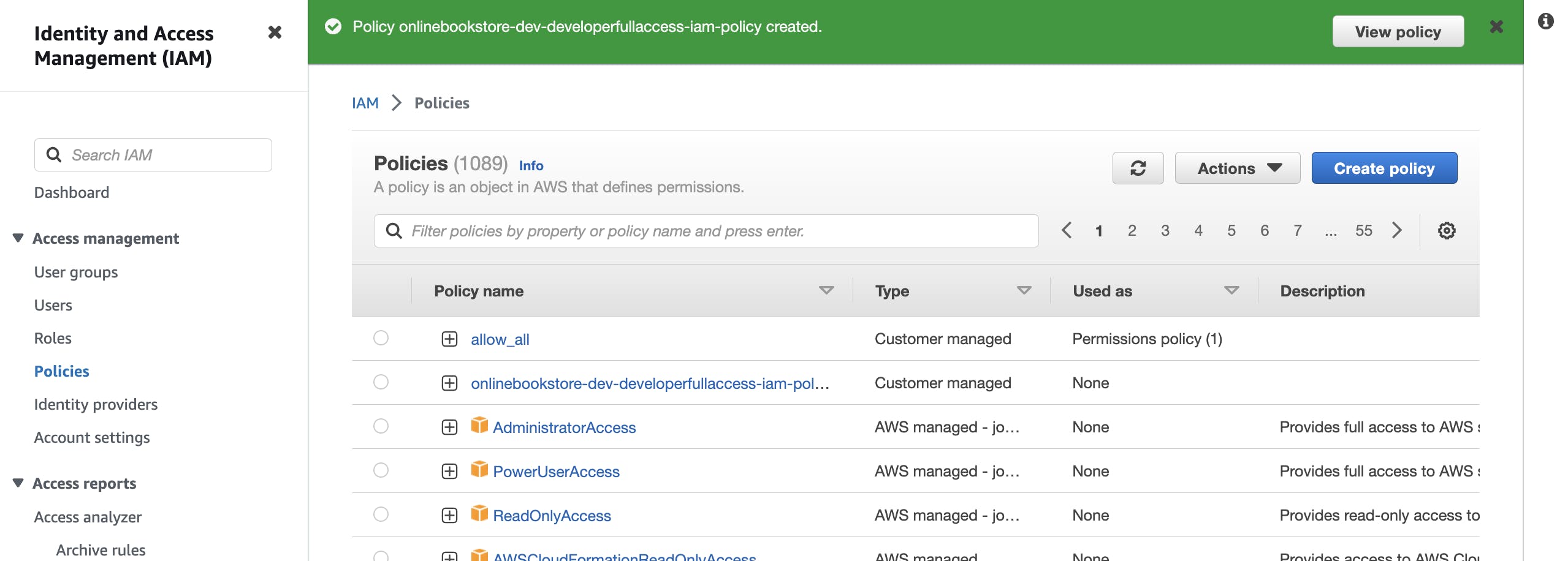
Now, we will create a group for developers, who will need access to the services we needed. So will make a group of developers and add the policy we created to that group.

Creating a group: Select the users who will need access.

Add a policy to that group we are creating:

Create a group:

Developers will have access for >> Dynamodb, Lambda, S3 bucket, API gateway
