#1 AWS Certified Solutions Architect - Associate (SAA-C03)
1️⃣ What is IAM?
Identity Access Management is used to manage users and manage access to users.
2️⃣ What is a "Root Account"?
The root account is the email address that you use to sign up for the AWS account, that account has all the administrative-level privileges.
Secure the root account:
↪️ Activate the MFA ( Multi-Factor Authentication) on the Root account.
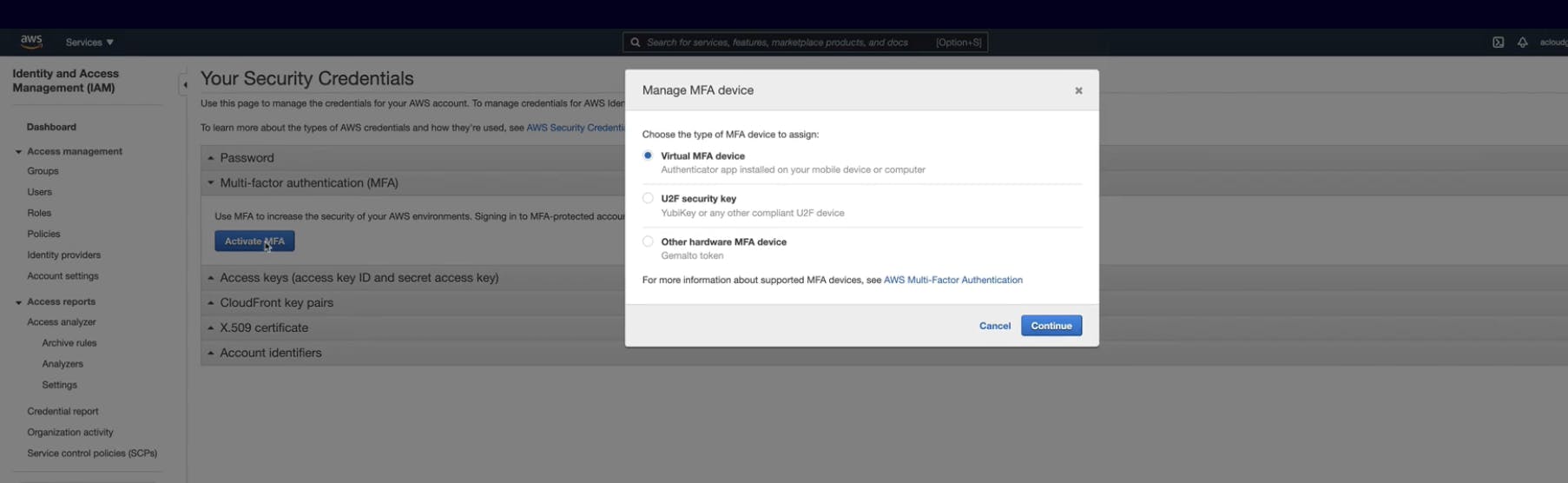
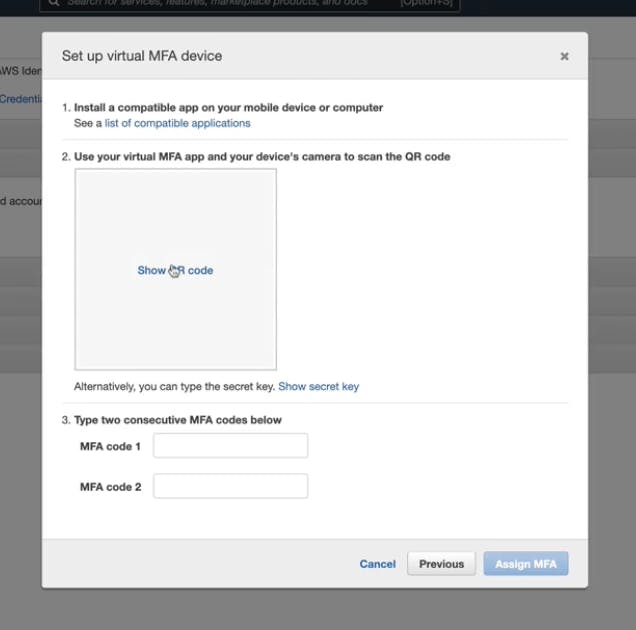
You can use Authenticator apps to pair up. Eg Google, Duo, Microsoft
3️⃣ Permission with IAM:
All the permissions in IAM are written in JSON Format (JavaScript Object Notation).
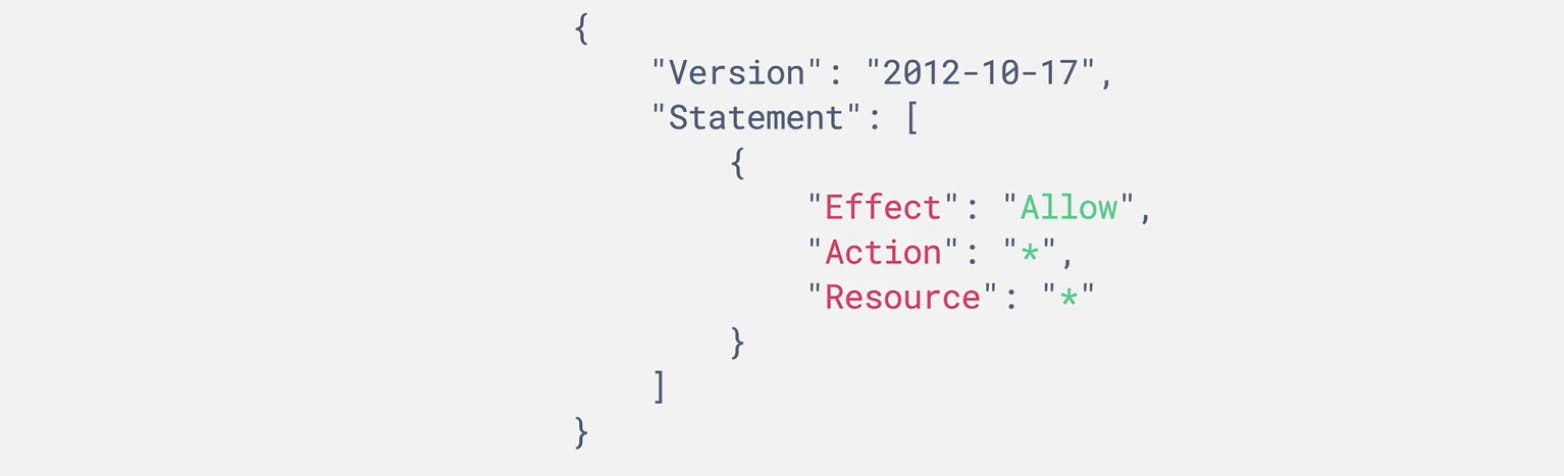
$Effect: Allow / Decline
$Action : ' * ' means allow all the users
$Resouces: ' * ' to access all the resources
4️⃣ What is the region?
A region is a geographical area, which contains availability zones. (always more than 2)
Suppose: Northern Virginia Region has 3 availability zone, then these AZ should be within 60 miles of each other.

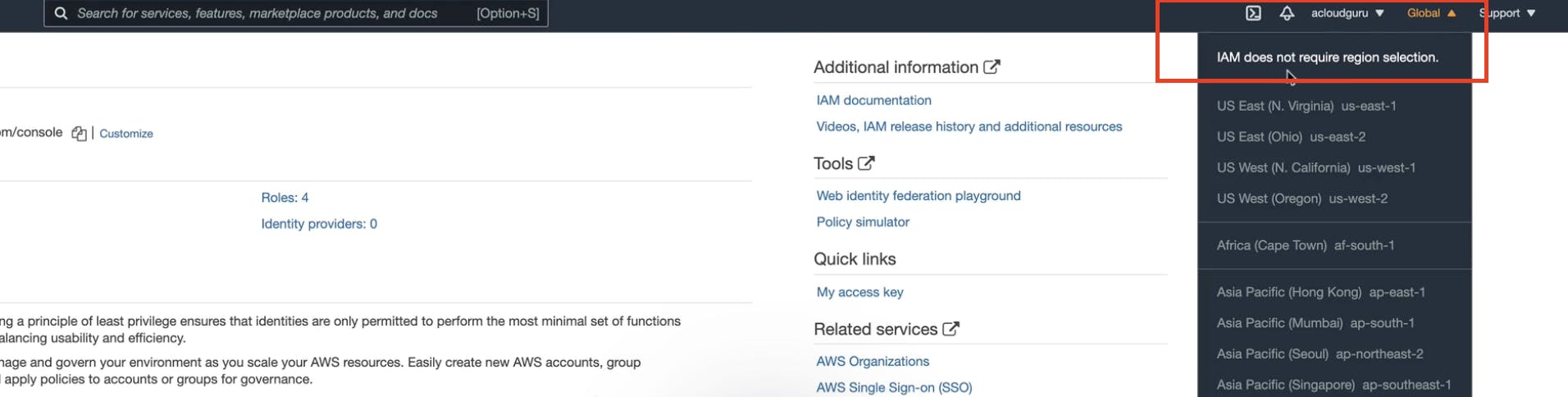
But, Policies are global-based, and not region based. IAM does not require region selection.
5️⃣ Adding Policies:
\>> Adding a user:

\>> Adding user to the group:
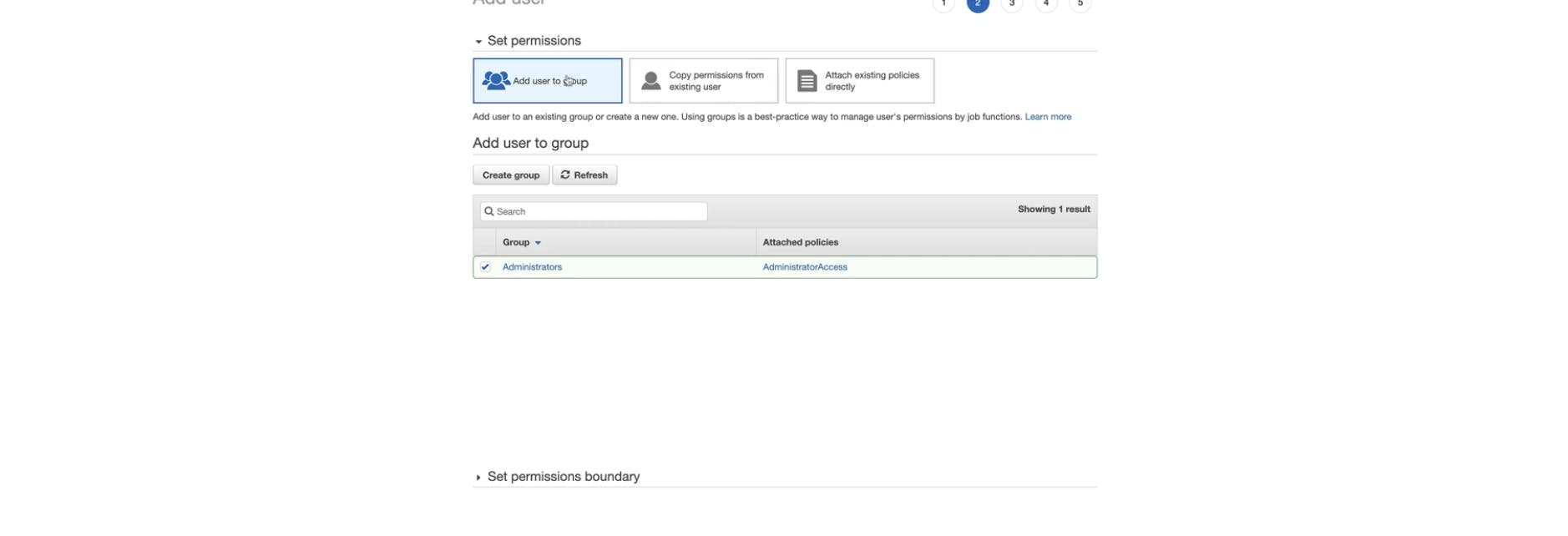
\>> Adding Administrator Access to that user:

Download the Secret Access key in CSV format.
6️⃣ Pre-Configured IAM policies:

The Data Scientists policy:


These are the Access to the following resources for the users.
6️⃣ Task:

Image source: A Cloud Guru
For more details:
AWS Identity and Access Management (IAM) serves as a solution for AWS clients to effectively control user permissions and access privileges for their accounts, alongside managing the available range of APIs and services within the AWS ecosystem. IAM's capabilities encompass the administration of user entities, as well as the management of security credentials, including API access keys, which in turn facilitates users' interaction with diverse AWS resources.
We will delve into the fundamental underpinnings of IAM. Our focus will be directed towards the aspects of user and group administration, and we will delve into the methodologies for allocating specific resource access by utilizing IAM-managed policies. Furthermore, we will acquire insights into the process of identifying the login URL, which is pivotal for AWS users to securely access their accounts. This exploration will be undertaken with a perspective grounded in real-world application scenarios.
